Part 8: Our observations about information systems
8.1
In this Part, we describe the trends, risks, and issues in the use of information systems by public entities. The comments are based on our observations during the annual audits in 2013.
8.2
We are seeing greater central direction for the management of information communications technology, greater use of shared services, an increase in the use of cloud computing services, and more staff wishing to use their own technology devices in their workplace. We note that government departments and Crown entities are aware of risks posed by their legacy systems and are taking steps to manage those risks. There is scope to better align business continuity plans with IT disaster recovery plans, and we also note that steps are being taken to strengthen the management of information security.
The scope of information systems audit work
8.3
The work carried out during an annual audit includes considering the information technology controls that affect the reliability of financial statements and service performance reporting. The work is carried out according to international auditing standards, in particular ISA (NZ) 315: Identifying and assessing the risk of material misstatement through understanding the entity and its environment. ISA (NZ) 315 gives auditors a framework to understand how entities operate and whether they have adequate controls in place to manage risks.
8.4
ISA (NZ) 315 states that the auditor should:
- carry out a risk assessment, including assessing the entity's internal controls;
- assess the risks of material misstatement within the financial statements;
- understand the entity and its environment, including its internal controls;
- communicate with those charged with governance; and
- document the understanding and the risks.
8.5
The auditors we appoint have teams of specialist information systems auditors. These teams perform audits of general information technology controls, business application controls, and data analysis. The work is not a comprehensive review of all information system controls. What gets audited depends on the results of an initial risk assessment, as well as an understanding of how the use of information systems affects the business processes that, in turn, have a material effect on financial statements.
General information technology controls
8.6
The specialist auditors draw on a range of frameworks to assess control risks. For example, Audit New Zealand uses an international framework published by the Information Systems Audit and Control Association called CoBIT.
8.7
An audit of general controls for information technology is split into two groups of work. First, a risk assessment is made of:
- governance and strategic planning;
- processes, organisation, and relationships;
- assessment and management of risks;
- how performance is monitored and evaluated; and
- the monitoring and evaluation of internal controls.
8.8
Secondly, the operational effectiveness of management controls (those that affect the reliability of financial statements and service performance reporting) is tested. This might include:
- systems acquisition and project management;
- security (network and applications);
- the management of physical hardware;
- change management;
- management of third-party services;
- management of data;
- management of operations;
- management of the configuration of the information communications and technology system; and/or
- management of problems and incidents.
Observations and matters arising from our audits
8.9
Information systems audits often identify areas for improvement and these are communicated in the auditor's report to the management of public entities. We have collated the audit reports for the central government sector to get a broader view of technology trends and risks.
8.10
As we noted in Part 1, public entities continue to maintain or improve services to the public in an environment of financial constraint. In response, many public entities have been looking at their use of technology to see how improvements and savings can be achieved.
Central direction for information communications and technology
8.11
There is an environment of change, driven by central direction and leadership from the Office of the Government Chief Information Officer (GCIO) in the Department of Internal Affairs. The role and influence of the GCIO continues to have a significant effect on the sector, with a strong emphasis on compliance and security as well as data classification and management.
8.12
The uptake rate for all-of-government contracts for Infrastructure as a Service26 is steadily increasing. It is not clear yet whether the anticipated cost savings will eventuate, and we expect entities to maintain a focus on benefits realisation.
Shared services
8.13
Public entities are increasingly sharing support services, such as financial management information systems or human resources systems. For example, the Treasury and the SSC are sharing a financial management information system, and the Inland Revenue Department is extending its financial management information system to deliver shared transactional services for the Department of Internal Affairs.
Cloud computing
8.14
Cloud computing means computer services provided remotely by suppliers through the Internet. One advantage of cloud computing is that users do not have to buy or invest in hardware, such as servers.
8.15
Cloud computing has been an increasingly important topic within technology departments as public entities look to deliver services in a more effective and efficient manner. This is actively encouraged in central government, with Infrastructure as a Service agreements in place with some suppliers. Our auditors have seen a significant increase in the use of Infrastructure as a Service by government departments, with others planning to move to it during the next 12-18 months.
8.16
Cloud computing is a service-based procurement model. Arrangements can be complex, with business structures that include overseas third-party organisations, which can be a challenge for establishing robust controls.
Bring your own device
8.17
Staff in many public entities are asking whether they can bring their own technology devices (such as mobile phones and tablets) to use in the workplace. This is referred to as "bring your own device". Strong policies and practices are needed before staff can bring their own devices, to cover compatibility as well as security.
Anytime, anywhere access
8.18
With the uptake of ultrafast and mobile broadband, there is a greater expectation that users of government services will be able to access their information and transact at any time of the day from any location in the world using any device they choose. There continues to be pressure on infrastructure and applications to be available 24 hours a day, seven days a week.
Risks for public entities in their use of information technology
8.19
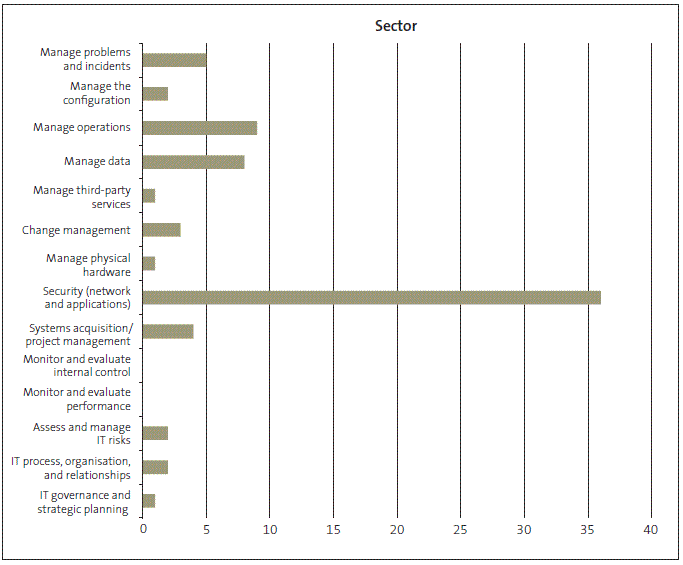
Figure 29 shows the audit exceptions from Audit New Zealand's information systems audit work, which is carried out as part of the annual audits. Audit exceptions are matters that the auditor notes that warrant asking the entity about. The Figure shows how often audit exceptions were identified during information systems audits. It covers only the public entities that Audit New Zealand is appointed to audit on behalf of the Auditor-General.
8.20
The high number of audit exceptions for security is, in part, because of the focus and time that the audits tend to devote to security issues. There are a high number of security tests.
8.21
Our other audit service providers have noted audit exceptions for change management controls, system developer access, and issues with legacy systems where entities rely on a small number of staff with historical knowledge to operate those systems.
8.22
The following sections discuss the main technology risks that we identified during our annual audits.
Figure 29
Number of audit exceptions noted during Audit New Zealand's information systems audits, 2012/13
Information security
8.23
Information security remains the area where most of our recommendations for improvement are made. Weak password settings, failure to promptly terminate system access, and periodic user access rights review are the most prevalent deficiencies identified.
8.24
Information security is inherently risky. This risk is likely to increase as systems become more complicated and more unsupported devices, such as devices owned by staff, are used in the work place.
8.25
Responsibility for security processes and controls is often spread throughout public entities rather than with a small group of individuals with clear accountability. This can increase the likelihood of controls failing. We have also observed that risk management principles and accountabilities are often not connected to information systems security-related activities.
8.26
Public concern about information security increased after inadvertent releases of private information at the Ministry of Social Development and EQC. More focus has already been given to improvement as a result.
8.27
The Government Communications Security Bureau is implementing a work programme to improve its information security. Its focus is on four primary controls – patching applications, patching operating systems, minimising the number of users with administrative privileges, and whitelisting27 applications.
Legacy systems
8.28
Legacy systems are older computer systems or programs that continue to be used, often because of the costs of replacing or redesigning them.
8.29
If legacy software runs only on antiquated hardware, the cost of maintaining it could eventually outweigh the cost of replacing both the software and the hardware – unless some form of backward compatibility allows the software to run on new hardware.
8.30
Legacy systems remain a concern for some public entities. We have found that the government departments with legacy systems are aware of the risks and taking steps to mitigate them. There is often a need for significant investment to change the legacy systems because they are often important operational systems. Examples include the Inland Revenue Department's tax system, FIRST; the Ministry of Social Development's payment system, SWIFTT; and the payment applications at the Ministry of Health.
8.31
Government departments continue to investigate the options available. Currently, the trend is to keep the legacy systems while any further changes are developed in new applications that interface with the legacy systems.
Business continuity and IT disaster recovery
8.32
Business continuity and disaster recovery remain an inherent risk to all government departments. There needs to be close alignment between the disaster recovery plans and business expectations set out in the business continuity plans. Government departments making use of Infrastructure as a Service also need to consider how these systems can be recovered in the event of vendor failures.
Mergers, amalgamations, and changes to structures of public entities
8.33
From an IT perspective, mergers often present several challenges to integrating systems from entities that have been operating independently for several years. Efficiencies anticipated from these mergers are not always realised as soon as forecast, or at all, if the IT systems cannot be successfully merged. There is often a dependence on the organisation redesigning its processes to ensure success.
Formalising the strategic direction of IT architecture and expenditure
8.34
Most departments have documented their IT direction and spending for the medium term (3-5 years) in their ICT strategies. However, there is scope for better strategic planning that takes into account the current all-of-government initiatives under way, such as procurement, shared services, and cloud computing options. Information systems are also significant assets for public entities, and we have found varying levels of benefits realisation management to maximise the value of information systems architecture and expenditure.
8.35
We are observing the spread of new technology trends, such as cloud computing and "bring your own device" policies, as government departments better understand the effect these technologies have on them.
Dependence on key skills
8.36
Public entities are under pressure to keep adequate numbers of skilled staff to maintain their systems. This is due to having legacy systems for which support skills have dwindled over time and competing with other employers in other sectors and countries.
Managing the services of vendors
8.37
As more public entities enter outsourcing arrangements for their IT infrastructure and services, there is a greater need to ensure that they are clear on what services they expect to receive. As the trend towards contracting the operation of IS systems, processes, and controls to third parties increases, the issues of who is accountable and who is responsible for what needs to be clearly defined. Public entities remain accountable for managing risks, and should have formal vendor management processes in place to monitor service levels and obtain assurance that the reported service levels are accurate.
26: One of the main categories of cloud computing service. A model in which entities pay an external provider to supply the equipment used to support operations, including storage, hardware, servers, and networking components.
27: A whitelist is a list of applications for which permission has been granted by the user or an administrator. Applications that are not on the list will not run.
page top